Ako Ransomware Uses Spam to Infect Its Victims
Source: Bleeping Computer / Lawrence Abrams
January 15: It has been discovered that the network-targeting Ako ransomware is being distributed through malicious spam attachments that pretend to be a requested agreement.
Last week it was reported that the Ako Ransomware was targeting companies with the intent to encrypt their entire network. At the time, it was not known how it was being distributed and when we asked the ransomware operators they told us it was a “secret”.
Since then, the ransomware identification site ID-Ransomware has seen an increasing amount of victims.
David Pickett, a Senior Cybersecurity Analyst at AppRiver, reached out to BleepingComputer yesterday to tell us that his company saw the Ako ransomware being distributed through spam email.
These emails pretend to contain an agreement requested by the recipient and use mail subjects such as “Agreement 2020 #1775505”.
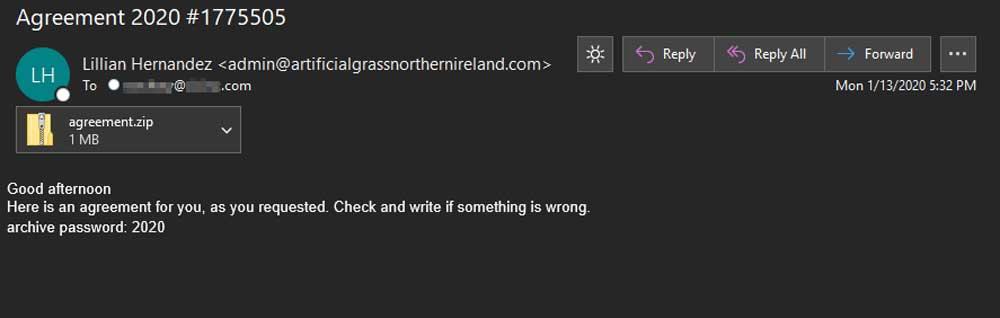
Attached to these emails is a password-protected zip file named agreement.zip with the password ‘2020’ being given in the email.
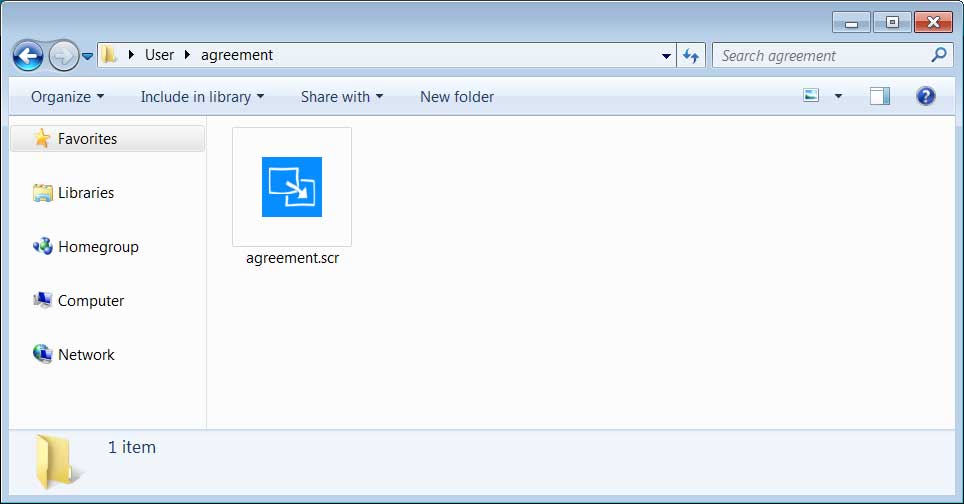
The extracted archive will contain an executable renamed as agreement.scr that when executed will install the ransomware.
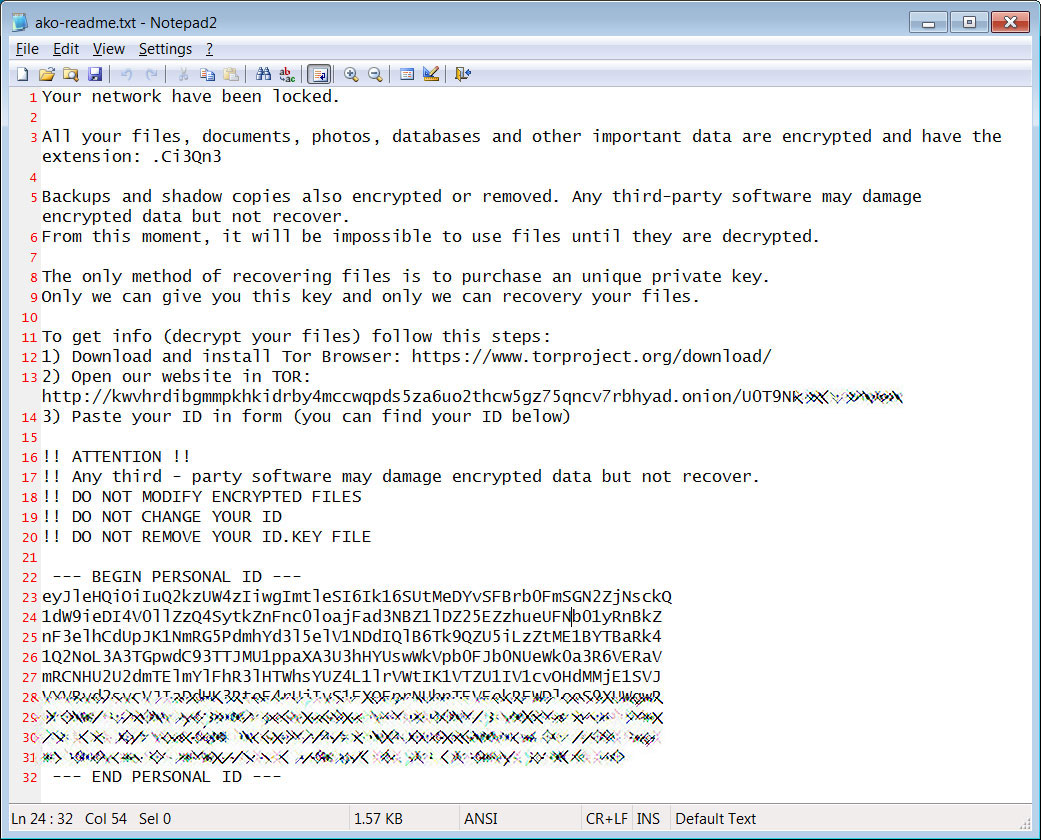
As shown by this report from JoeSandbox, when Ako is executed it will encrypt the victim’s files and leave them with a ransom note named ako-readme.txt.
As spam is being used to spread the Ako Ransomware, everyone must be is trained on how to properly identify malicious email and not open any attachments without first confirming who and why they were sent.
This is especially true for email attachments that are in password-protected archives as they commonly used to avoid being detected by secure email gateways and antivirus software.

