FTCode Ransomware Now Steals Saved Login Credentials
January 20: FTCode ransomware victims now have one more thing to worry about with the malware having been upgraded to also steal saved user credentials from email clients and web browsers.
FTCode is a PowerShell-based ransomware strain first spotted in 2013 by security researchers at Sophos, a malware that resurfaced in October 2019 as the final payload in a spam email campaign targeting Italian recipients.
Being fully developed in PowerShell allows it to encrypt its targets’ devices without having to download additional components, while also making it very easy for its developers to add new functionality.
The ‘new and improved’ FTCode ransomware
The newly added info stealer functionality allows FTCode to harvest and exfiltrate the stored credentials before encrypting its victims’ files.
FTCode is now capable of stealing saved credentials from both web browsers (Internet Explorer, Mozilla Firefox, Google Chrome) and email clients (Mozilla Thunderbird and Microsoft Outlook).
The way the ransomware collects the credentials is different for each of the five applications, directly accessing registry keys in the case of Internet Explorer and Microsoft Outlook, while in the case of Mozilla Firefox, Mozilla Thunderbird, and Google Chrome it goes into the folders where the apps store the credentials.
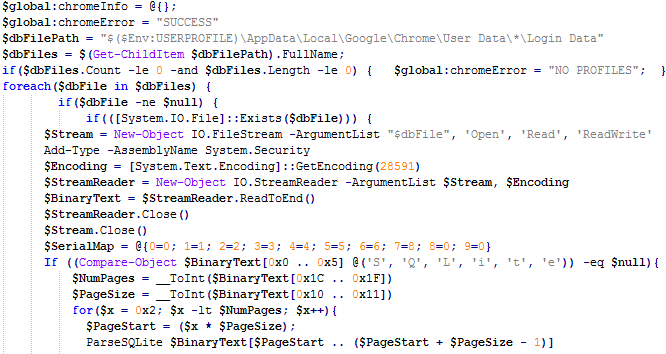
Once the information is harvested, FTCode will deliver it to its operators using a POST request sent to its command-and-control (C2) server, with the usernames and passwords being encoded using the Base64 encoding scheme.
This capability was not available in previous variants as confirmed in a report published by researchers with the Zscaler ThreatLabZ team.
An FTCode Decryptor for those who can capture the encryption keys while having their computers encrypted is available from Certego.
FTCode brought back to life
Starting September 26th, a series of reports [1, 2, 3, 4] about new ransomware being distributed via spam and named FTCode.
Security outfit Certego said that it is was the sample Sophos detected in 2013 and speculates that FTCode was revived in recent attacks because PowerShell is integrated by default on Windows devices running at least Windows 7 or Windows Server 2008 R2.
The FTCode ransomware arrives on its victims’ computers via spam emails containing malicious Word documents camouflaged as invoices, document scans, and resumes, which will drop the JasperLoader malware downloader and then encrypts the device.
However, the encryption will not happen until the malware will gain persistence by adding a scheduled task and a shortcut into the Startup folder.
Right before starting to encrypt the files, FTCode will check for the C:\Users\Public\OracleKit\w00log03.tmp file that acts as a killswitch.
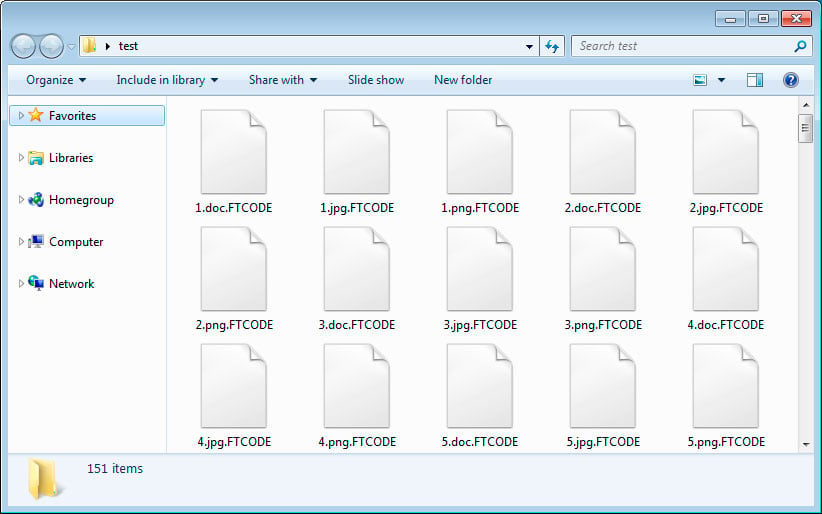
If that file is not found, FTCode generates an encryption key that gets sent to the attackers’ C2 server, an encryption key that can be captured and later used with Certego’s decryptor to restore files on locked computers.
In the next stage, the ransomware also disables the Windows recovery environment and deletes Shadow Volume Copies and Windows backups to make data recovery impossible without paying the ransom.
Next, FTCode starts encrypting files adding the .FTCODE extension to all locked files and READ_ME_NOW.htm ransom notes to every folder.
The attackers ask for $500 ransom to deliver the decryptor to their victims, however, as one of BleepingComputer’s readers has pointed out there have been reports of paying the ransom and not getting the decryptor.

